11 Jan

How to Host a Secure Zoom Meeting
In just over nine months, Zoom has gone from a convenient videoconferencing tool into a household brand name. As business travel, events, and offices around the globe shut down rapidly due to the COVID-19 pandemic, Zoom’s suite of videoconferencing functions have provided an essential lifeline that have allowed everyone from educators to CEOs to late-night talk show hosts continue to connect with peers, customers, students, and friends and family. The variety of users who need to host a secure Zoom meeting these days numbers in the millions, a remarkable rise for the company.
However, while Zoom has made significant improvements to security features since the spring, keeping Zoom meetings secure and uninterrupted still requires some careful use of privacy and security features. Security issues have always been a part of videoconferencing apps, but the widespread adoption of Zoom puts a particular spotlight on some of the more notable flaws that have been exposed as more and more of the world have adopted the platform.
Key Zoom Security Issues You Should Know About
Zoombombing – Perhaps the most widely publicized security issue involved the trend of “Zoombombing” – a catchy name for people logging into Zoom meetings (either uninvited or under an alias) and sharing inappropriate images or messages in the chat box, sharing illicit images or videos using the screen-share function, or unmuting their microphones to say or play inappropriate audio. Zoombombing gained special notoriety because of a variety of incidents during remote education, where young students attending classes were exposed to inappropriate content while teachers looked on helplessly.
Encryption/Data Routing Concerns – Similarly troubling were early revelations that sensitive Zoom meetings might be routed through unsecured servers. Without end-to-end encryption (which Zoom now offers thanks to the uproar surrounding this issue), people were able to easily access private information of users in meetings, as well as content from the meetings themselves.
Vulnerabilities for Phishing/Hacking – Over the course of the year, numerous security weaknesses (from fabricated GIFs to issues with meeting recordings saved in the cloud) have forced Zoom to constantly push new security updates to close loopholes and protect user privacy. While the gaping security concerns that emerged earlier in the year seem to be well in the past, the continued emergence of small loopholes that allow phishing and hacking opportunities only reinforce the need for a dedicated focus on using meeting controls and privacy features to ensure your virtual meetings are protected.
How to Host a Secure Zoom Meeting – 10 Steps Every Host Should Take

While privacy is a real concern when using Zoom, the good news is that Zoom has rolled out a ton of useful updates and privacy/security controls that can prevent 99% of the issues that we noted above. The trick for users is to know which tools are essential to prevent potential security issues, and which steps you should take when creating and setting up your meeting to protect yourself and your meeting attendees.
It’s also important to remember that free Zoom accounts do not offer many of the more enhanced and useful privacy features. You need to pay for a monthly Pro (or higher) account to gain full access to different privacy and security features that can truly protect your meetings.
With that in mind, here are ten essential steps to host a secure Zoom meeting:
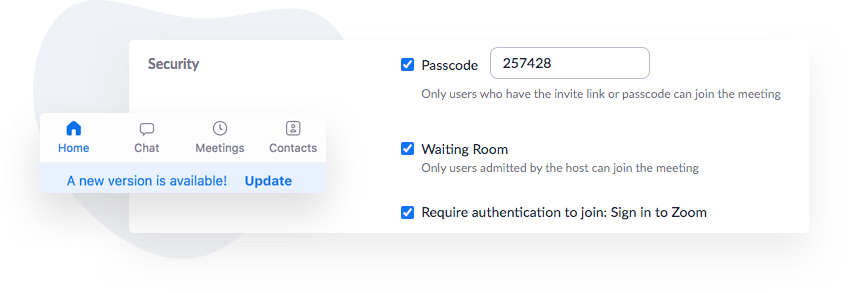
- Password Protection – The easiest way to avoid unwanted guests is to ensure that users need to enter a unique passcode for your meeting to join in the first place. Just like for your own accounts, the more detailed and complex the password, the better. Remember also that while you may only share your meeting invite and password with your guest list, once the email is sent, you don’t have control over who they send it to. It is worth reminding guests that passwords are private, and warn guests that they may be held accountable for unauthorized sharing of meeting passwords (especially if the meeting is covering private or sensitive issues).
- User authentication – More recently, Zoom rolled out two-factor authentication (2FA), following the trend of other major tech platforms in requiring multiple identity checks to make it even more difficult for unauthorized users to attend meetings. 2FA requires users to present two or more “credentials” (methods of confirming identity) to authenticate ownership of a Zoom account before entering the meeting. These factors include passwords, fingerprints, or other hard-to-falsify data points.
- Randomly generated unique IDs – The ability to create unique 10 or 11-digit meeting IDs for each new meeting is another layer of protection for hosts. Reusing meeting IDs is one of the easiest ways to let unwanted guests attend, so creating a unique meeting ID for especially sensitive meetings (instead of using a recurring meeting) is always good idea.
- Waiting room feature – One of the earliest security additions Zoom added is the waiting room. Users must wait in the room until admitted by the meeting host, which lets the host vet the ID of anyone seeking entry. Additionally, hosts can communicate with users in the waiting room, allowing you to contact and ask security questions if needed to prove the user is who they say they are.
- Meeting lockdown – Once all expected guests have been granted access, hosts have the ability to lock the meeting to any other entries by simply clicking on the Participant settings and toggling Lock Meeting.
- Disable the ability to join before the host – Many teachers learned the hard way during the early months of the pandemic that unauthorized users can wreak havoc in a meeting if they gain access before the host. When setting up your event, you can toggle this ability off – ensuring that you are able to join your meeting first and ensure security settings before any unwanted guests arrive.
- Restrict participant abilities – While Zoom offers participants a number of useful abilities (such as screen-sharing, user-to-user messaging, and the ability to record meetings), these features are often the most abused by Zoombombers. If you expect a large number of attendees you don’t know personally, it’s a good idea to turn off these features (which can be done by clicking on participant settings) to limit anyone from hijacking your meeting. You can always give these abilities back to your users if you need them by toggling them back on.
- Avoid file sharing – Just as many hackers gain access to computers through USB drives or emails with malicious files, file sharing in Zoom meetings offers an opportunity for hackers to access a host’s computer subtly. While file sharing may be necessary in certain meetings, disabling the function can prevent one of the easiest methods for security breaches.
- Remove attendees – If an attendee is acting inappropriately in your meeting, Zoom has a solution. You can remove an attendee for any reason, and removed attendees will need your permission and action to rejoin the meeting again.
- Always update whenever prompted – Like any tool, Zoom releases new security and privacy updates regularly, and in response to any newly discovered security breach or issue. Whenever you are asked to update your Zoom software, do it! The best way to host a secure Zoom meeting is to always use the most recent privacy and security features.
Other Considerations When Hosting Your Next Event with Zoom
Aside from the security and privacy features Zoom offers, there are also some practical steps you can take to ensure digital safety for yourself and your guests:Use an event management platform – The best event management platforms can offer you pre-emptive security features (like secure online invitations, guestlist management, and more) that can help you manage your Zoom event attendees and lower the risk of any uninvited guests before you even start your meeting.
Communicate expectations and rules with guests clearly – While you don’t need to lecture a small group of trusted co-workers, if you are hosting a Zoom event with hundreds of attendees you may not know, putting together a digital etiquette reminder email and sending it out to attendees beforehand can help prevent unintentional tech issues to help the meeting run more smoothly.
Gather feedback and learnings to make your next event more smooth – While some guests may be frustrated by overly protective security controls, one of the best ways to strike a balance between security and guest experience is to gather feedback. Find out from your guests if there are certain disabled features they’d appreciate in future meetings, and tailor your event security protocols accordingly!









